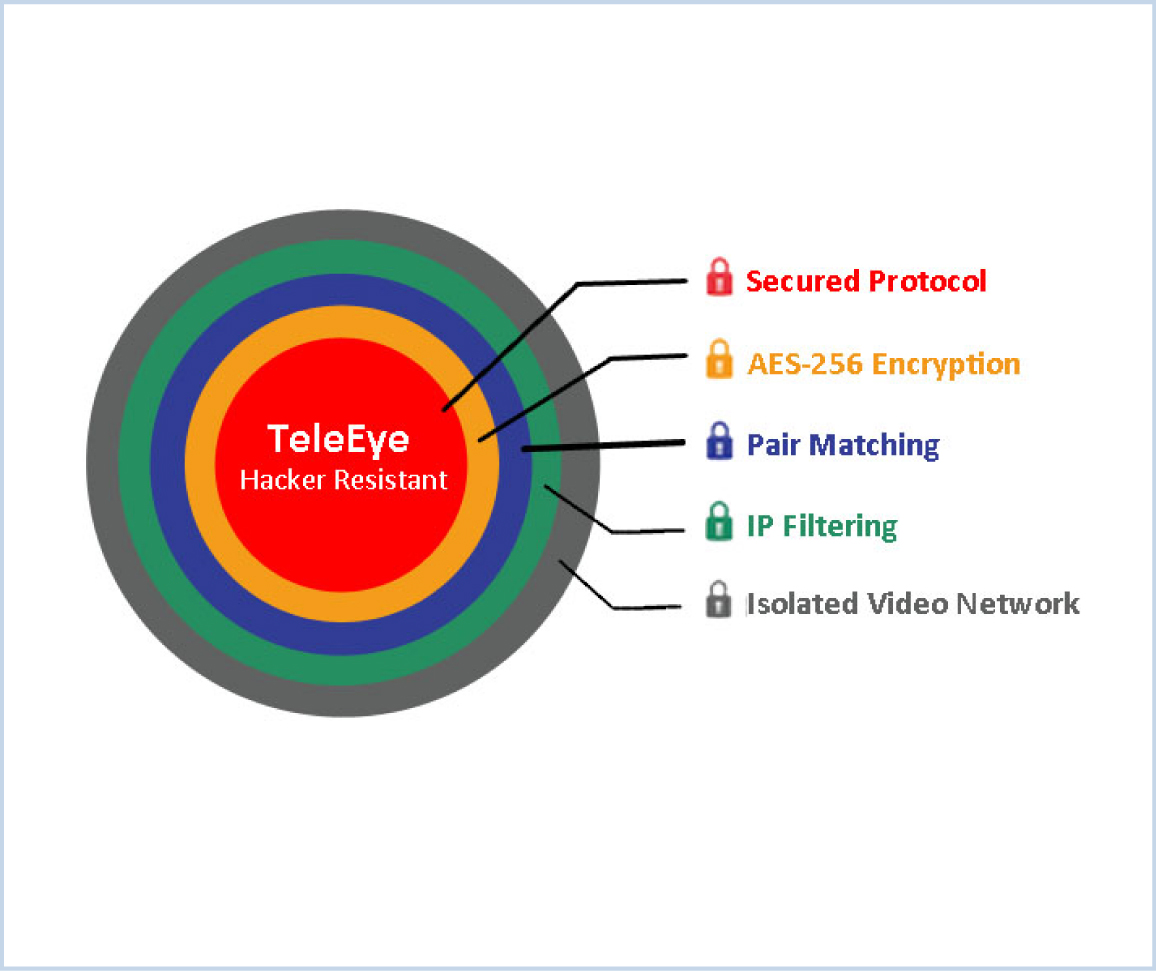
Hacker Resistant Technology
The majority of IP cameras available on the market are designed based on open standards, meaning their architectures are available on the internet for all to access. Whether it’s at home, in the office or in a shop, if you are using an IP camera then your video footage is at risk of being viewed by an unauthorised third party without your consent of knowing.
The TeleEye Hacker Resistant technology is incorporated into a range of TeleEye cameras and DVRs. TeleEye Hacker Resistant technology comprises of five layers of anti-hacking protection which are designed to prevent hackers from extracting confidential video data from your security camera, giving users a peace of mind.

Secured Protocol
TeleEye has developed special video streaming protocols that provide extra security during internet transmission.Hackers are not able to decode the captured data streams, as the TeleEye proprietary protocols are strictly confidential and inaccessible by unauthorised parties.

AES - 256 Encryption
TeleEye encrypts critical data using AES 256 bit encryption technology. the superior encryption design prevents hackers from understanding the data delivered through open platforms.

Pair Matching
TeleEye hardware and software are applications have individual identities to match with each other. Only a valid registered pair can log on to perform video management functions. In other words, other customers' non-registered TeleEye software is prohibited from gaining access to your security video systems.

IP Filtering
IP filtering restricts users only with designated IP address to gain access to your security camera network, whilst other unauthorised IP addresses are warded off automatically.

Isolated Video Network
The video network and the computer network are completely two different circuitry that they cannot mutually communicate. Therefore, the video footage is under an isolated layer that the authorized video data can only be forwarded through routing with management. As a result, the public network is unable to access to your internal video network and therefore the hackers can be completely cut off.

